
“Cross-Site Request Forgery (CSRF) is an attack that forces user to execute unwanted actions on a web application in which they’re currently Logged in.
What is CSRF (Cross-site request forgery)?
“Cross-Site Request Forgery (CSRF) is an attack that forces user to execute unwanted actions on a web application in which they’re currently Logged in. CSRF attacks specifically target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request. With a little help of social engineering attack, an attacker may trick the authenticated users of a web application into executing actions of the attacker’s choice. If the victim is a normal user, a successful CSRF attack can force the user to perform state changing requests like transferring funds, changing their email address. If the victim is an administrative account, CSRF can compromise the entire web application.”
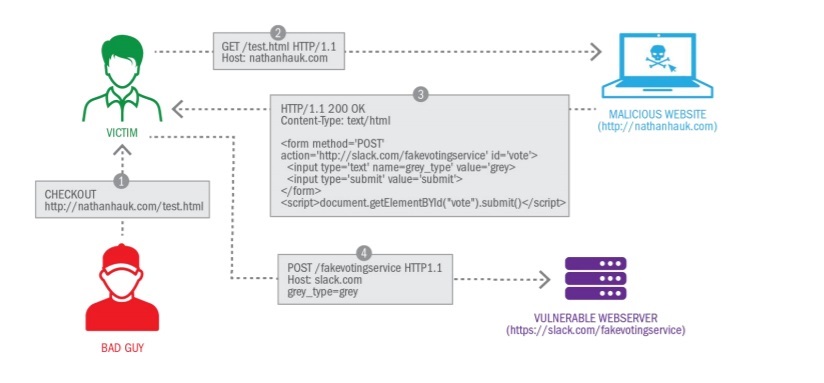
What is the impact of a CSRF attack?
In successful CSRF attack, the attacker causes the victim to carry out an action.
E.g.: Attacker can change victims Username, password or fund transfer depending on the action. Attacker can take over full account control of all application.
How CSRF work?
There are three conditions must be in place:
A relevant action. There is an action within the application that the attacker has to be a reason to induce. This might be a privileged action such as modifying permissions for other users or any action on user specific data.
Cookie-based session handling. Performing the action involves issuing one or more HTTP requests, and the application relies solely on session cookies to identify the user who has made the requests. There is no other mechanism in place for tracking sessions or validating user requests.
No unpredictable parameter requests. The requests that perform the action do not contain any parameters whose values the attacker cannot determine or identify.
For example, suppose an application contains a function that let the user change the email address on their account. When a user change email id, they make an HTTP request like the following:
POST /email/change HTTP/1.1
Host: example.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 35
Cookie: session=ydasasdad5eefwefw
email=admin@user.com
This meets the conditions required for CSRF:
1.The attacker can easily analyse the values of the request parameters that are needed to change.
2.Session cookie to identify which user issued the request. There are no other tokens.
With this HTML code attacker can design
With these conditions in place, the attacker can construct a web page containing the following HTML:
<html>
<body>
<form action="example.com/email/change" method="POST">
<input type="hidden" name="email" value="admin@user.com" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Preventing CSRF attacks:
1.Anti-CSRF tokens are considered the most effective method of protecting against CSRF.
2.Strictly validated in every case before the relevant action is executed.
Copyright @SecurWires. Designed & Developer By MindScript