
The CIS Controls are a recommended set of actions for cyber defense that provide specific and actionable ways to thwart the most pervasive attacks.
IT security leaders use CIS Controls to quickly establish the protections providing the highest payoff in their organizations. They guide you through a series of 20 foundational and advanced cyber security actions, where the most common attacks can be eliminated.
The CIS Controls are a recommended set of actions for cyber defense that provide specific and actionable ways to thwart the most pervasive attacks. The CIS Controls are a relatively short list of high-priority, highly effective defensive actions that provide a "must-do, do-first" starting point for every enterprise seeking to improve their cyber defense.
Prioritization is a key benefit to the CIS Controls. They were designed to help organizations rapidly define the starting point for their defenses, direct their scarce resources on actions with immediate and high-value payoff, and then focus their attention and resources on additional risk issues that are unique to their business or mission.

The Payment Card Industry Data Security Standard (PCI DSS) is a set of Best Practices to improve the security of cardholder information throughout the processing lifecycle. The PCI Standard is mandated by the card brands and administered by the Payment Card Industry Security Standards Council (PCI SSC). The standard was created to increase controls around cardholder data to reduce card frauds.

Data Security Standard adopted by major card processing networks (Visa, MasterCard, JCB, Discover, and Amex) to combat fraud and promote secure processing of payment card transactions. PCI DSS is a Unified standard for security associated with card data storage, transmission, and processing. Depending on different geographies, local regulators enforce PCI DSS compliance.
The Payment Card Industry Data Security Standard (PCI DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally. PCI DSS provides a baseline of technical and operational requirements designed to protect account data.
PCI DSS applies to ALL entities involved in Payment Card Processing – including Merchants, Processors, Acquirers, Issuers and Service Providers. PCI DSS also applies to ALL other entities that Store and/or Process and/or Transmit CardHolder Data (CHD) and/or Sensitive Authentication Data (SAD).
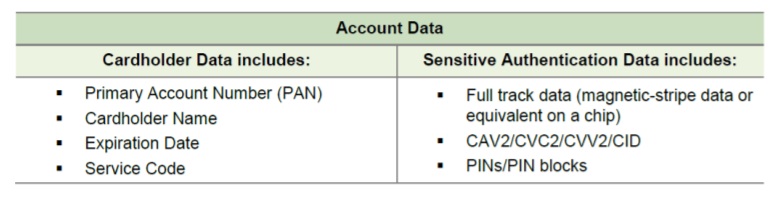
Account Data, CardHolder Data (CHD) and Sensitive Authenticable Data (SAD)
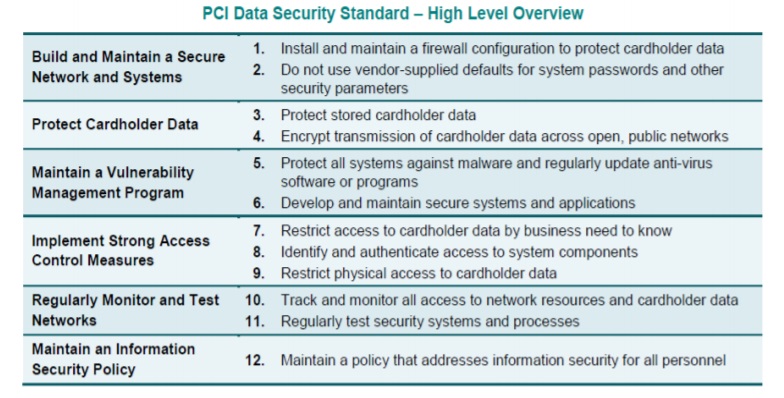
The Data Security Standards consists of 6 Major Goals which are further divided in 12 Requirements. Each requirement addresses the specific set of Information Security Domains which covers all aspects of Security – Information Security Policy and Procedures, Awareness, Risk Assessment, Network Security, Telecommunication Security, Server Security, Wireless Security, End User Computing, Remote Access, Data Security, Data Handling, Data Encryption, Malware Controls, Vulnerability Controls, Secure Software Development Life Cycle, Access Control, Identification and Authentication, Database Security, Physical Security, Backup Security, Log Management and Monitoring, Time Synchronization, File Integrity Controls, Intrusion Detection or Prevention Control, Security Testing (Vulnerability Assessment, Penetration Testing etc.), Incident Response, People Security and Third Party Security.
PCI DSS comprises a minimum set of requirements for protecting account data, and may be enhanced by additional controls and practices to further mitigate risks, as well as local, regional and sector laws and regulations. Additionally, legislation or regulatory requirements may require specific protection of personal information or other data elements (for example, cardholder name). PCI DSS does not supersede local or regional laws, government regulations, or other legal requirements.
The CIS Controls are not a replacement for any existing regulatory, compliance, or authorization scheme. The CIS Controls map to most major compliance frameworks such as the NIST Cyber Security Framework, NIST 800-53, ISO 27000 series and PCI DSS.
Copyright @SecurWires. Designed & Developer By MindScript